Access to AWS, faster and more secure.
Get production access instantly to fix things when you're on-call.
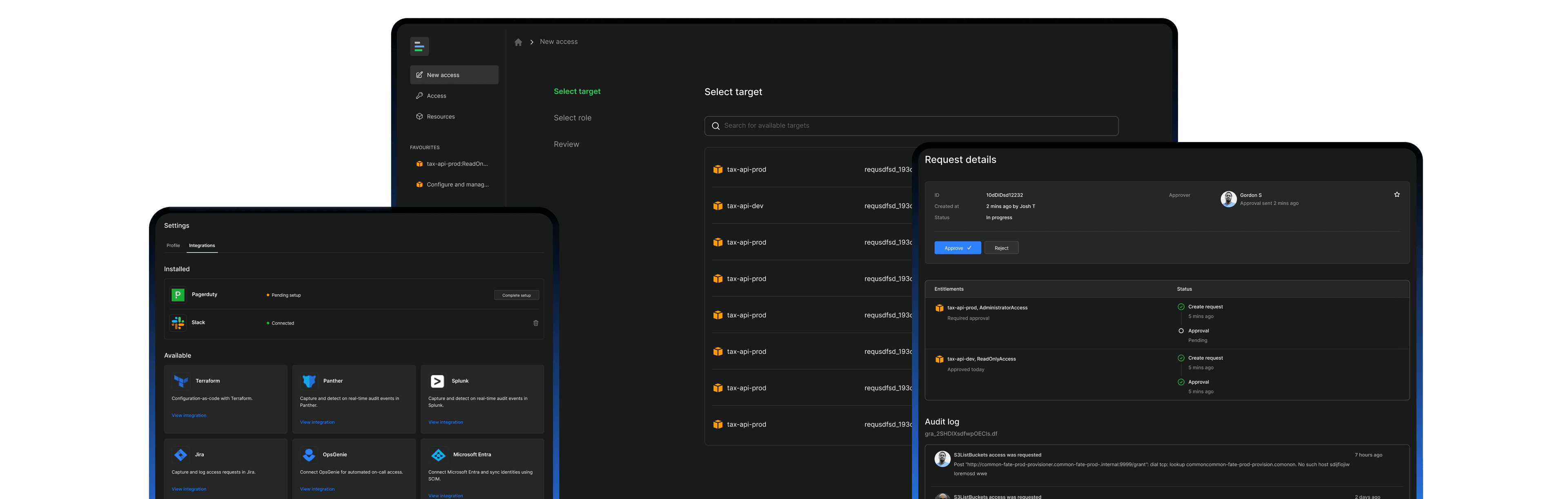
Common Fate helps you protect your most sensitive digital assets, and ensures that the right people have access to them at the right time.
Protect sensitive data in the cloud
Implement least privilege access controls and secure access to sensitive production accounts and customer data.
Optimize developer velocity and security posture
Speed up and empower employees with automated access workflows. Safely provision access based on configurable access policies and contextual checks such as on-call status or an employee's department.
Bring-Your-Own-Cloud (BYOC) deployment
Avoid giving the keys to your kingdom away to a SaaS provider. You can optionally deploy Common Fate to your own cloud environment. All data and automation flows remain entirely in your own cloud.
Key Features
Common Fate is an identity security solution designed for cloud native teams.
Privileged Access Management
Safely provision fine-grained and time bound access to production accounts just-in-time across AWS and GCP.
Secure Database Access
Implement access control over all databases from a single pane of glass. Flexibly manage and audit all access to company data, right down to a specific row in a database.
SAML SSO, by default
SAML SSO, user and group syncing are included in all plans.
Policy-as-Code
Use Terraform to define authorization policies. Use your existing CI/CD system to test and deploy them.
Insights
Identify, quantify and understand identity risk across your cloud environment. Track risk reduction over time.
Identity Provider Integration
Common Fate integrates with your existing identity provider such as Okta or Microsoft Entra to provision access.