
Blog
Updates and Insights

Chris Norman • 15 April 2025
Common Fate is winding down
Today I have an important update to share: Common Fate is winding down operations.
Company Updates
Chris Norman • 4 October 2024
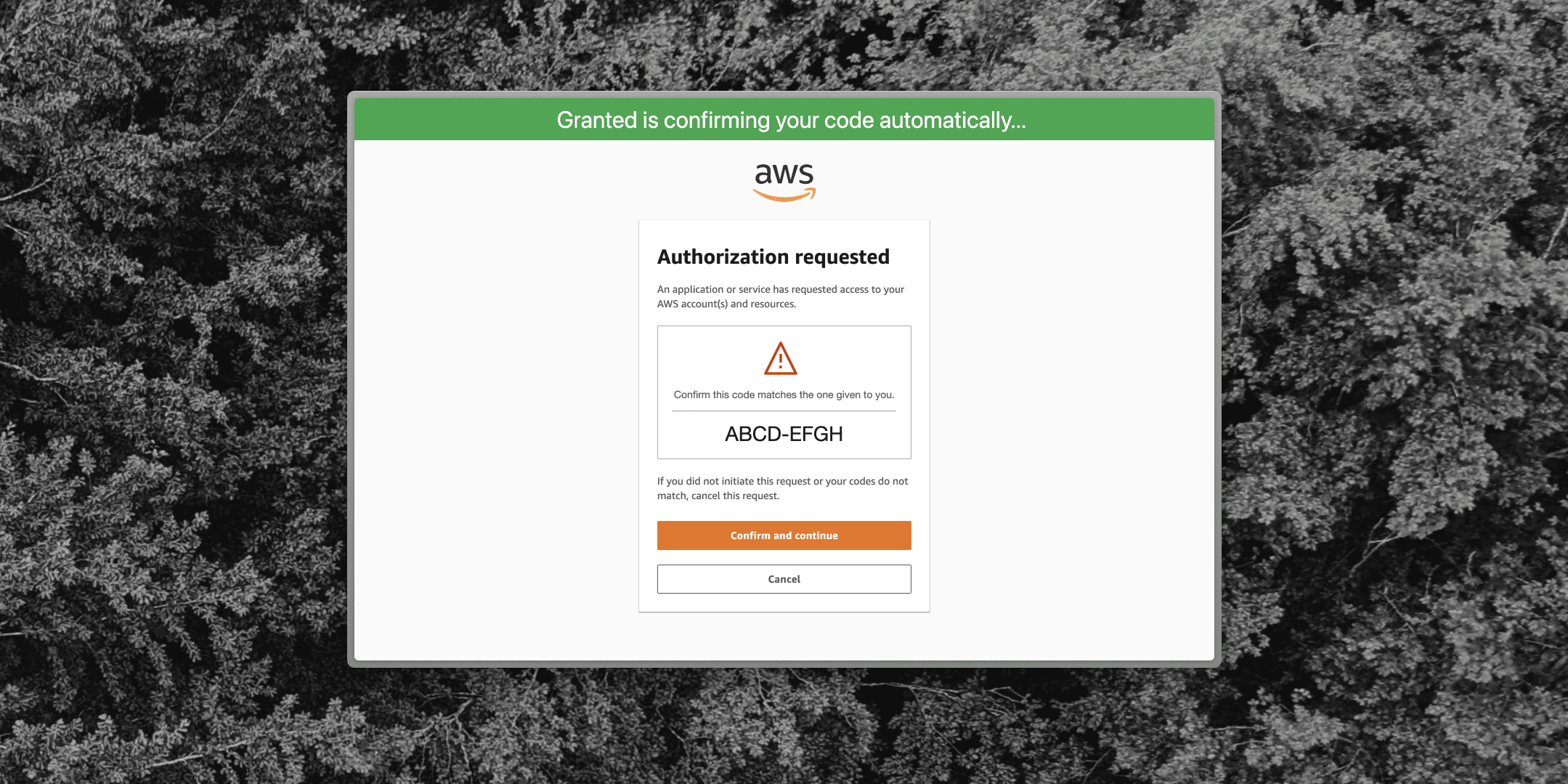
Granted now mitigates device auth phishing in AWS IAM Identity Center
Today we're releasing a new browser extension for Granted which makes authenticating to AWS IAM Identity Center faster and more secure.
Product Updates
Rowan Udell • 29 August 2024
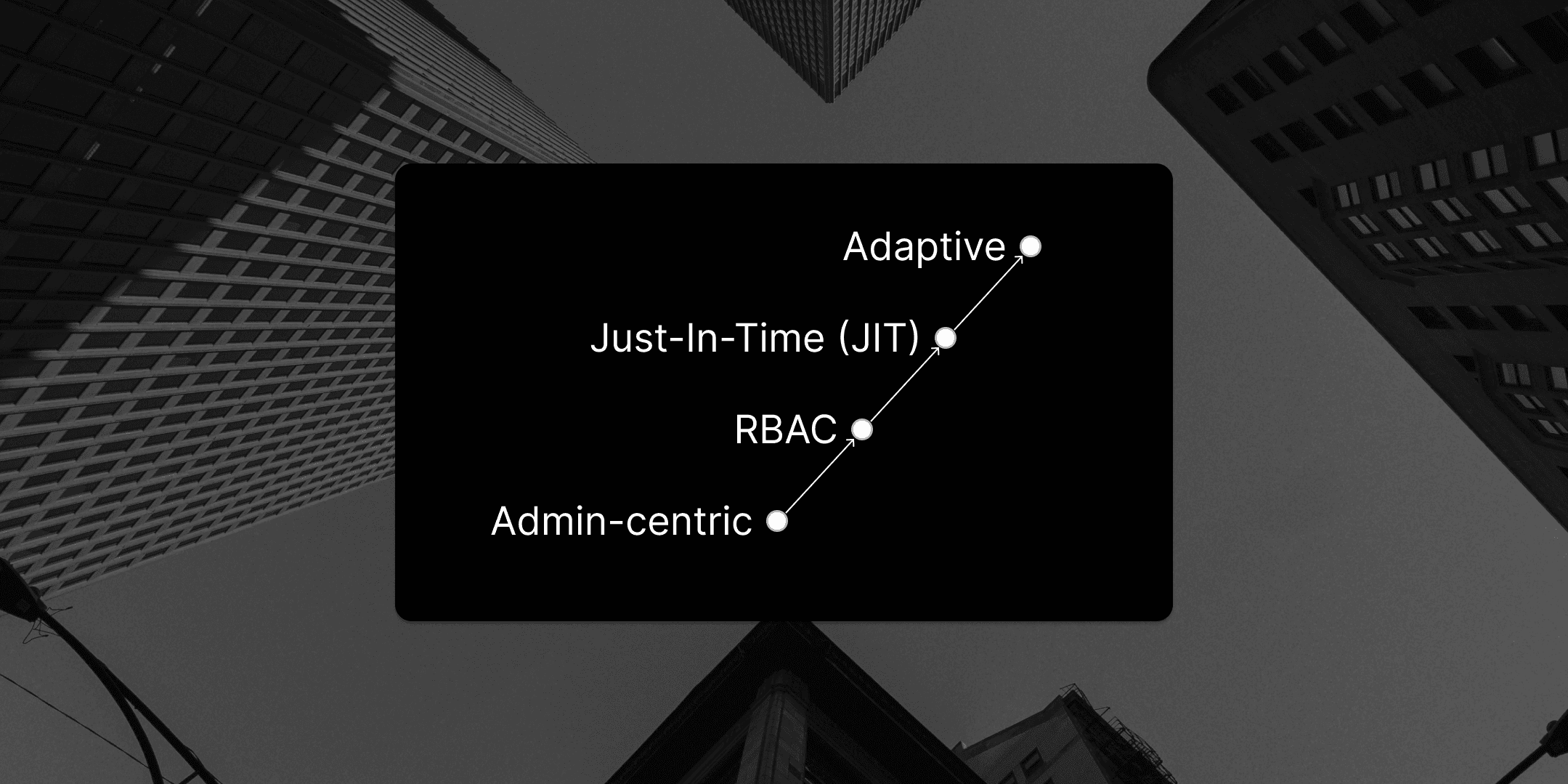
A Cloud Access Management Maturity Model: Part 2
Metrics to manage and improve to raise maturity
Community
All Blog Posts