Today we're releasing a new browser extension for Granted which makes authenticating to AWS IAM Identity Center faster and more secure. The extension protects users from being phished for AWS credentials.
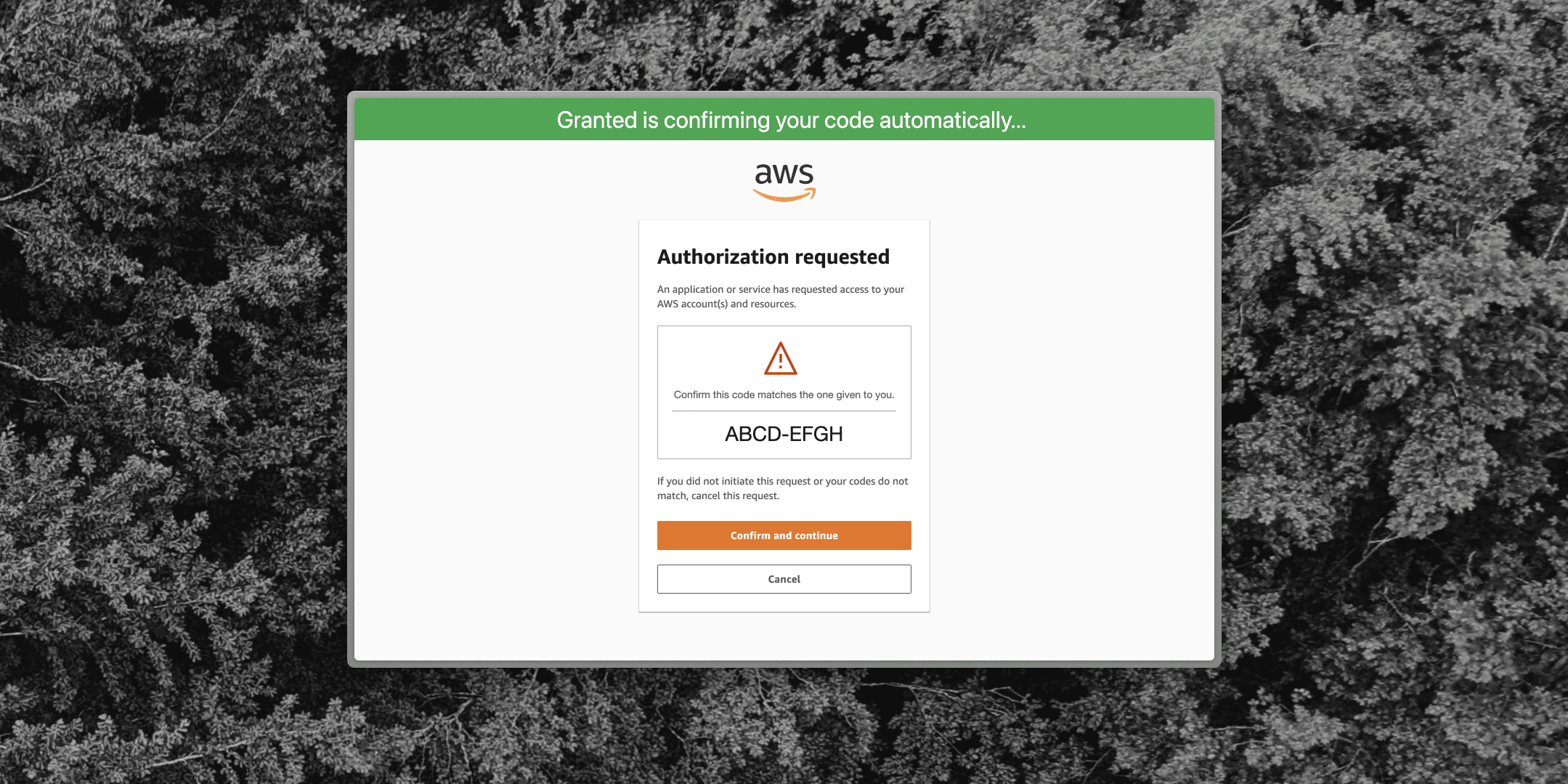
When users authenticate to IAM Identity Center using a CLI, a browser window like the below is opened. Clicking "Confirm and continue" begins a login flow where users are prompted to authenticate using their single-sign on credentials, including entering MFA.
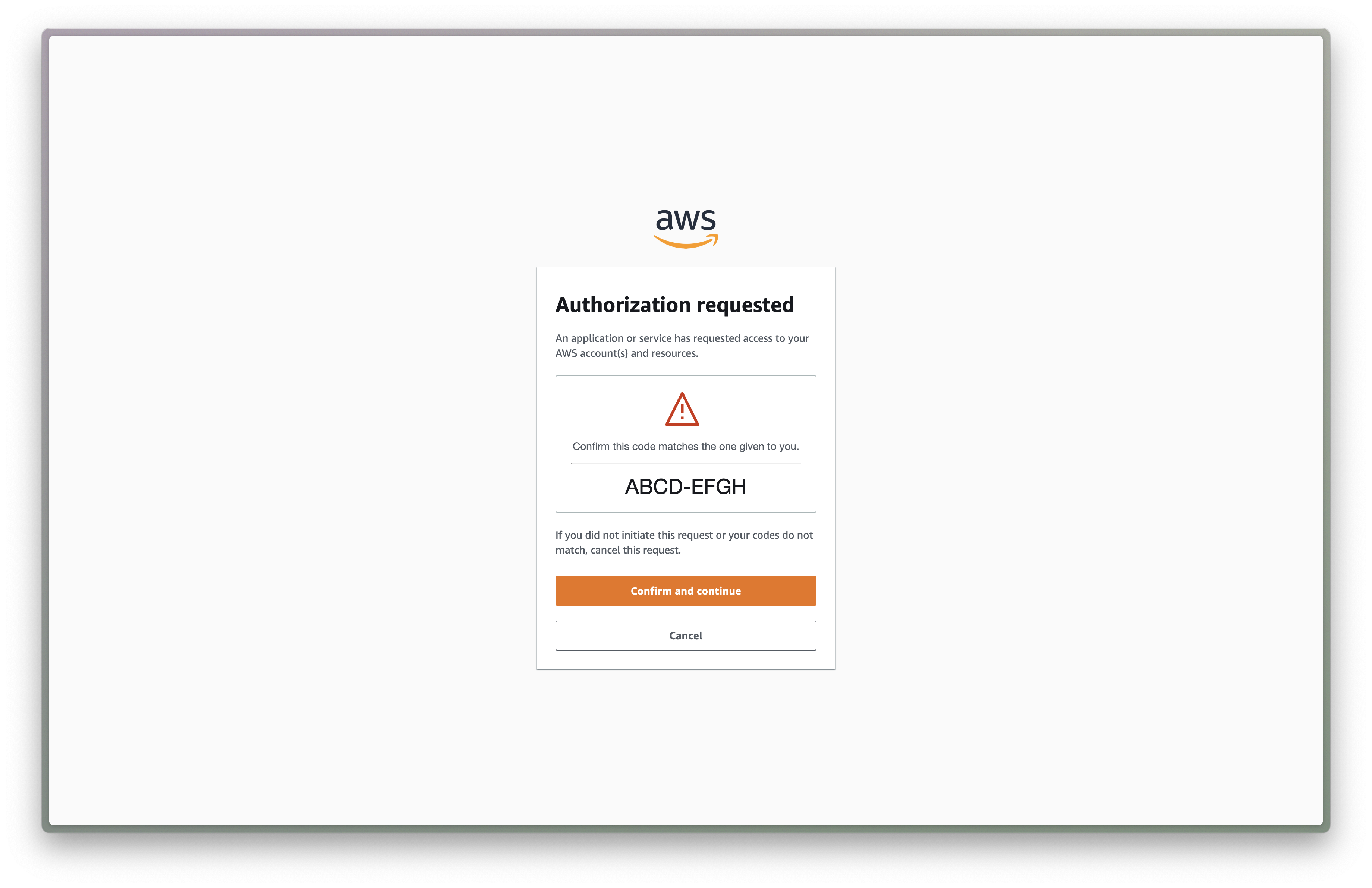
The problem with this process though is that an attacker who knows your IAM Identity Center URL can craft a malicious login URL and send it to you. If you're unlucky enough to open it, this is what you'll see:
Looks similar to the first screenshot, right? And what's worse, if you click "Confirm and continue" here and enter your SSO credentials, the attacker will gain access to all of the AWS roles available to you in IAM Identity Center.
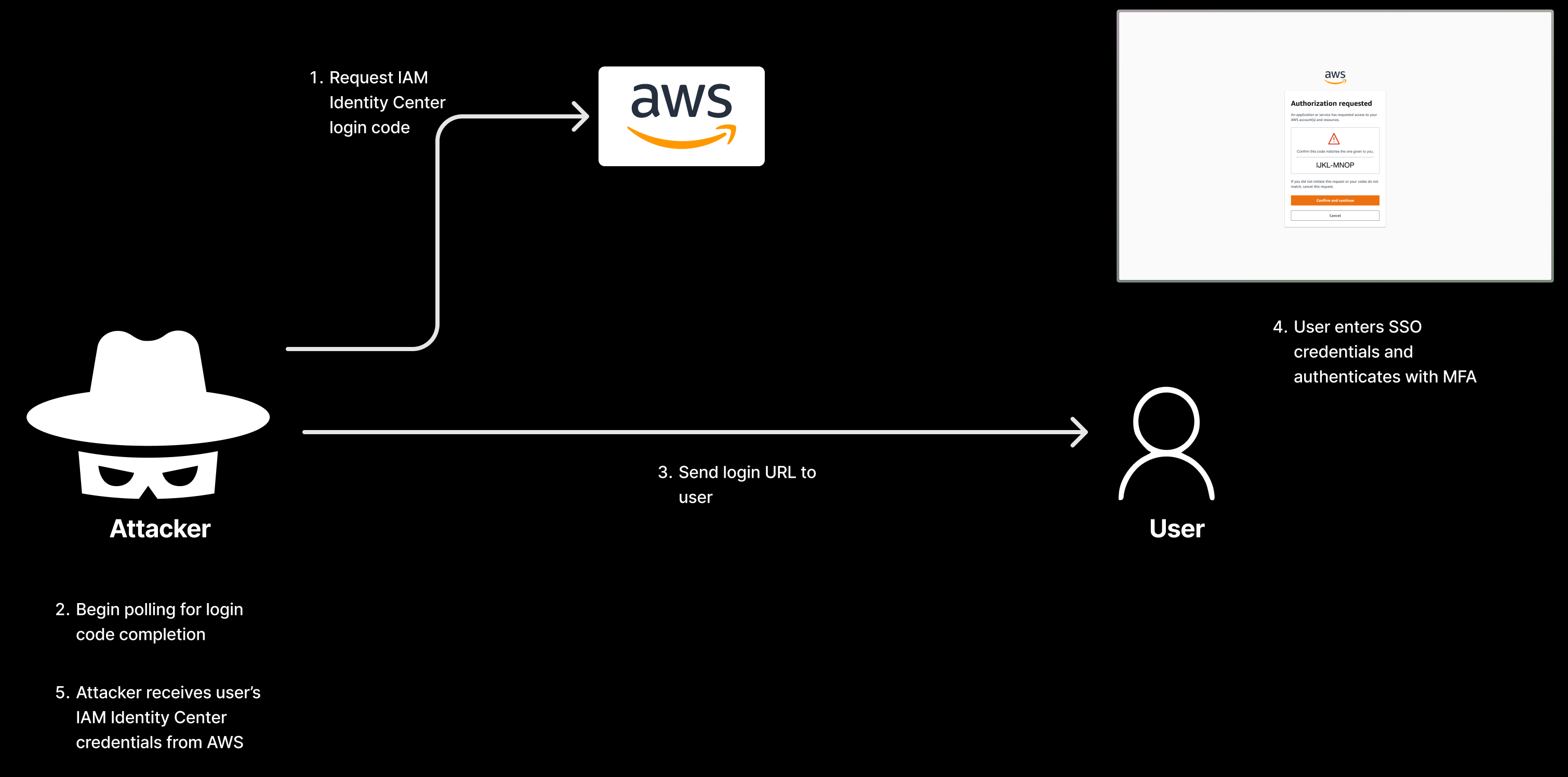
Sebastian Mora has created a proof-of-concept for the attack here.
How Granted helps
The Granted browser extension reads the code on the IAM Identity Center confirmation page and confirms that it matches the Granted CLI. If the code matches, the extension clicks the "Confirm and continue" button on your behalf. This makes the login process faster.
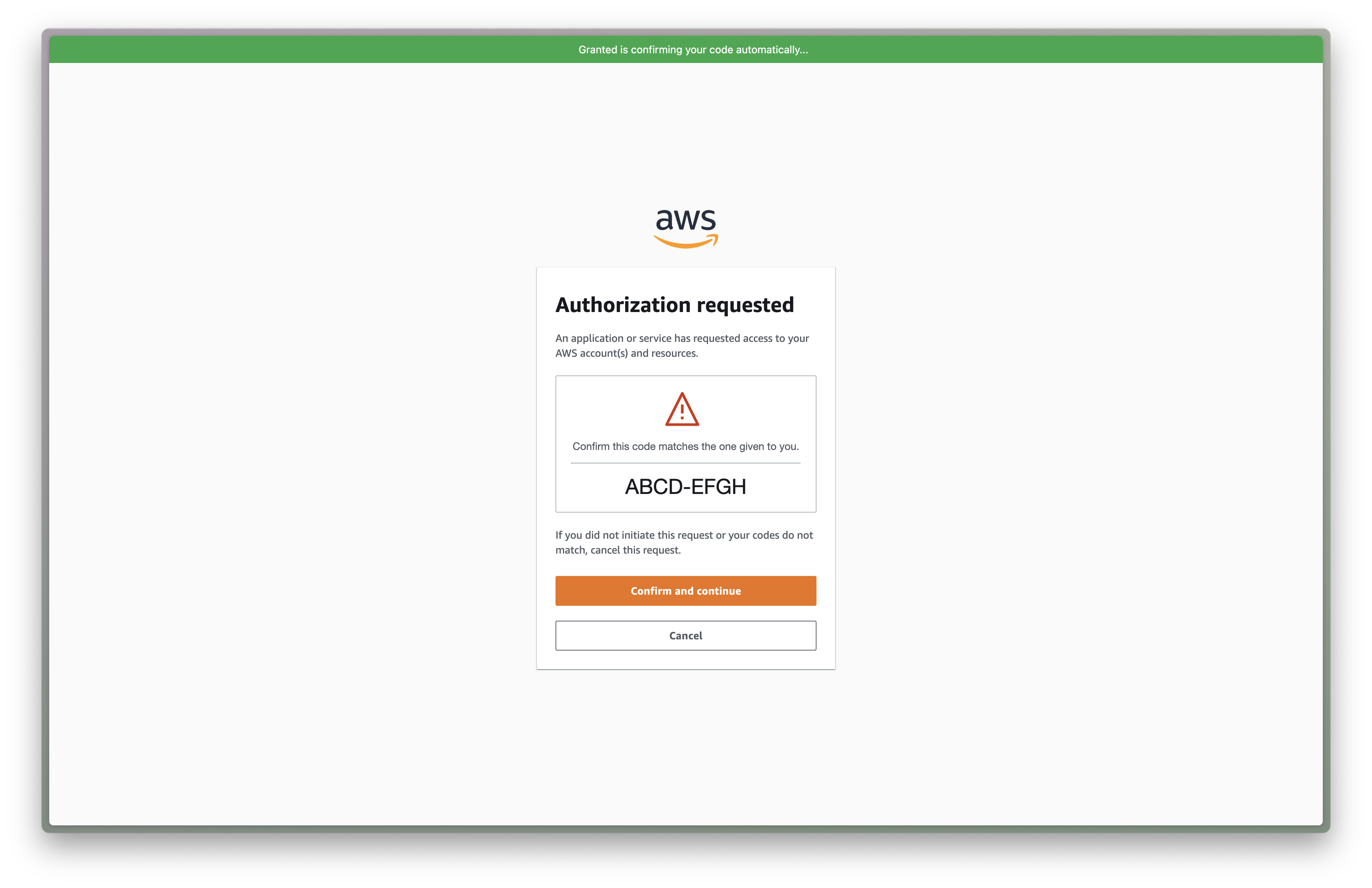
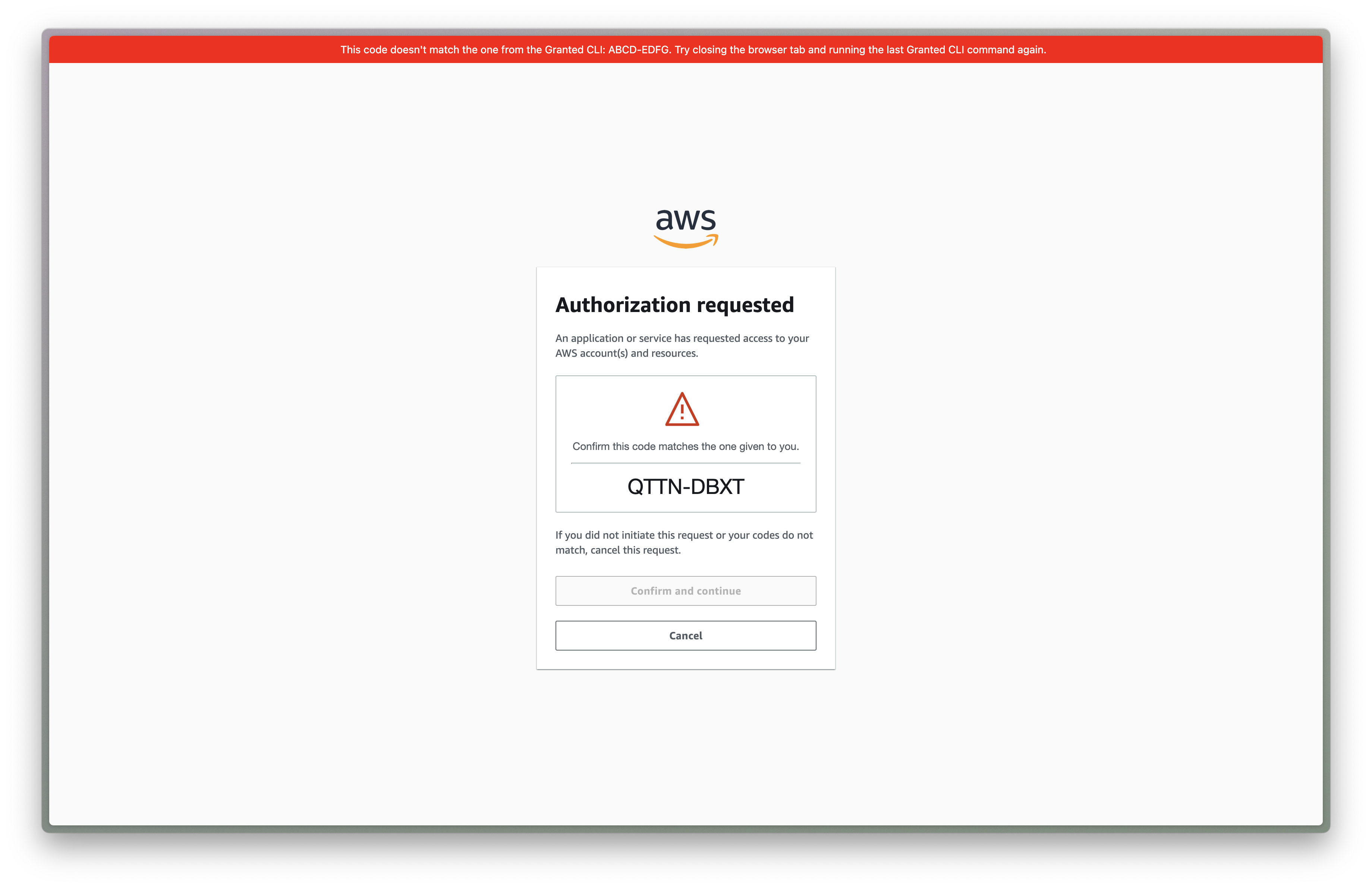
If you're ever sent a malicious login URL by an attacker, Granted disables the confirmation button to prevent your credentials being stolen.
Under the hood, the browser extension uses the native messaging API to communicate with the Granted CLI. Using native messaging means that other browser extensions or applications can't read the user code from Granted.
The extension works in all Chromium-based browsers and requires Granted version 0.35 or later.
A big thanks to Rami McCarthy - this feature originated from a discussion I had with Rami at fwd:cloudsec EU last month where he suggested we build this into Granted.