Today we have released Common Fate CLI v1.15. This release adds support for running Access Tests.
Access Tests allow you to verify the behaviour of authorization policies and confirm that Common Fate resource syncing is working as expected. You can write tests to check for invariants, such as "an external contractor should never have auto-approved production access", or "a security team member should have auto-approved access to an account in the Security Organization Unit in AWS".
Access Tests are specified using a YAML file, similar to the following:
# group-tests test whether a user is a member of a group or not.
group-tests:
- user: alice@example.com
group: 2df6c5c4-0e09-477a-b796-9ad9bd756d83
is-member: true
# access-tests test whether a user is allowed to access a particular entitlement or not.
access-tests:
- user: alice@example.com
target: development-aws-account
role: AWSReadOnlyAccess
expected-result: auto-approved
- user: alice@example.com
# you can also use Cedar entity IDs here for the target or role
target: AWS::Account::"123456789012"
role: AWS::IDC::PermissionSet::"3d06e8e5-93d3-4bfd-ae4f-e5caf43c99ad"
expected-result: requires-approval
- user: alice@example.com
target: very-sensitive-aws-account
role: AWSReadOnlyAccess
expected-result: no-access
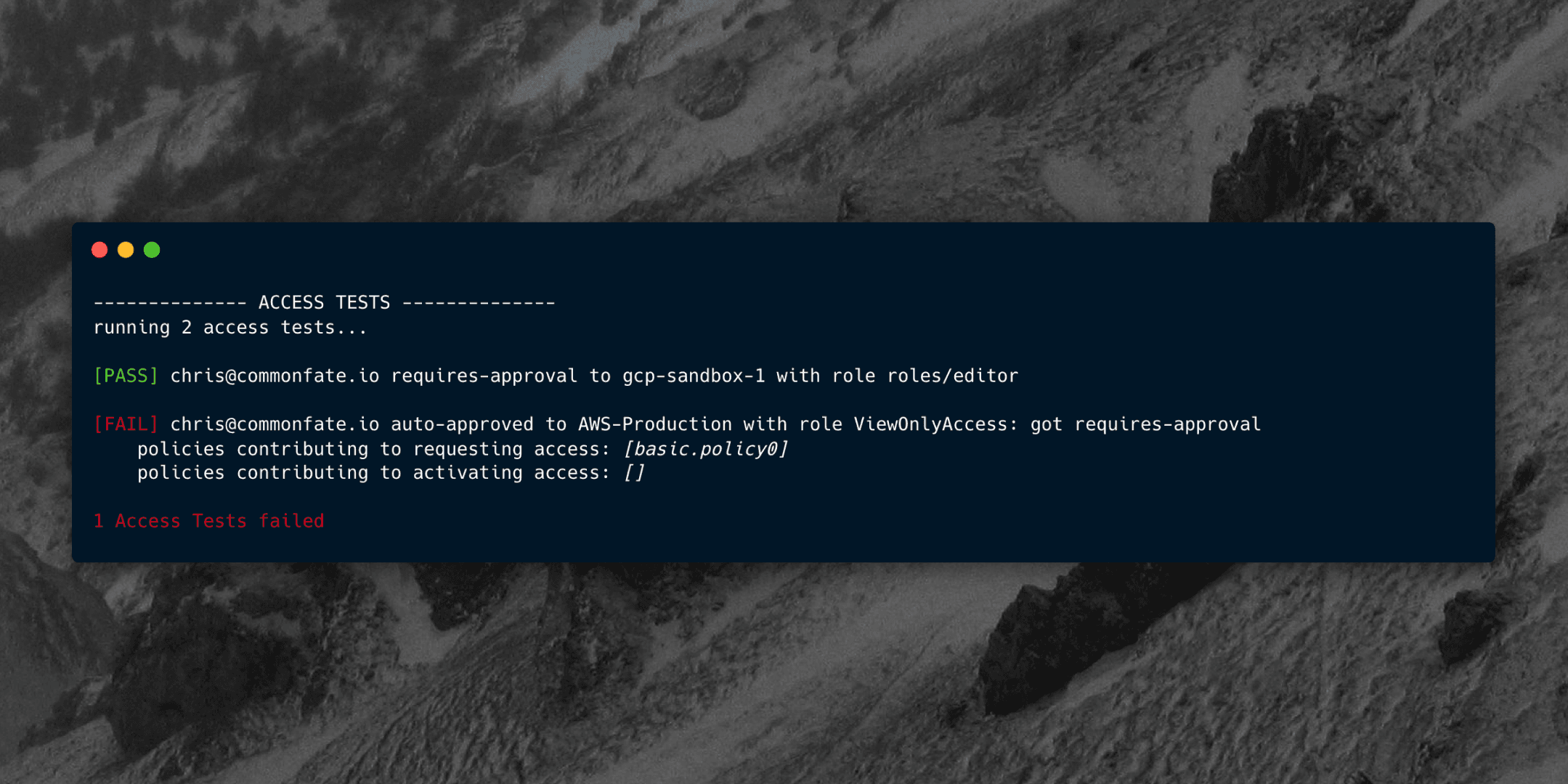
You can run tests by using cf tests run -f tests.yml. You'll see an output similar to the below:
retrieving users for email address lookups...
retrieved 126 users
-------------- ACCESS TESTS --------------
running 2 access tests...
[PASS] chris@commonfate.io requires-approval to Sandbox-1 with role ViewOnlyAccess
[FAIL] chris@commonfate.io auto-approved to Sandbox-2 with role ViewOnlyAccess: got requires-approval
policies contributing to requesting access: [basic.policy0]
policies contributing to activating access: []
-------------- GROUP MEMBERSHIP TESTS --------------
running 2 group membership tests...
[PASS] chris@commonfate.io is member of c9bed4d8-d091-7057-4ed7-6d60bcf1e8bf
[PASS] chris@commonfate.io is not member of 790e94a8-2071-7016-a43c-86e66212a43d
1 Access Tests failed
All Group Membership Tests passed
You can also run tests in Continuous Integration providers like GitHub Actions. Here's an example GitHub Actions workflow:
name: Test
on:
push:
jobs:
access:
name: Access Testing
runs-on: ubuntu-latest
steps:
- name: Checkout
uses: actions/checkout@v4
- name: Install Common Fate CLI
uses: common-fate/install-cli-action@v1
with:
oidc-client-id: abcdefGHIJKL12345678 # replace this with your Client ID
oidc-client-secret: ${{ secrets.CF_OIDC_CLIENT_SECRET }}
oidc-issuer: https://cognito-idp.us-east-1.amazonaws.com/us-east-1_abcdeFGH # replace this with your Issuer
api-url: https://commonfate.example.com # replace this with your Common Fate API URL
- name: Run Access Tests
run: cf tests run -f tests.yml
To learn more about this feature, read our documentation on access testing.