Don't like reading? Check out a demonstration here.
It’s 4:30pm on a Friday afternoon. There are 52 access request tickets in your Security kanban board. One of your policy guys spent a week putting together a template for permission requests, but no one actually cares enough to use it. Over half the tickets don’t have the Reason field filled out, and even fewer have specified a Duration. While setting up permissions for one user, you notice that a pentester you contracted two years ago still has cloud admin access.
The newest DevOps hire is already considering going back to college. The Risk team has given up. Even the CISO can barely afford her therapy bills anymore. You try to blink away the tired, but it only makes your eyes burn more.
It’s 5pm on a Friday afternoon. There are 51 access request tickets in your Security kanban board.
If your job is anywhere adjacent to cloud security, then this has probably been you at some point. Maybe this is you right now. But what if we told you that there’s a better way — and that it’s free and open source?
Introducing: Granted Approvals.
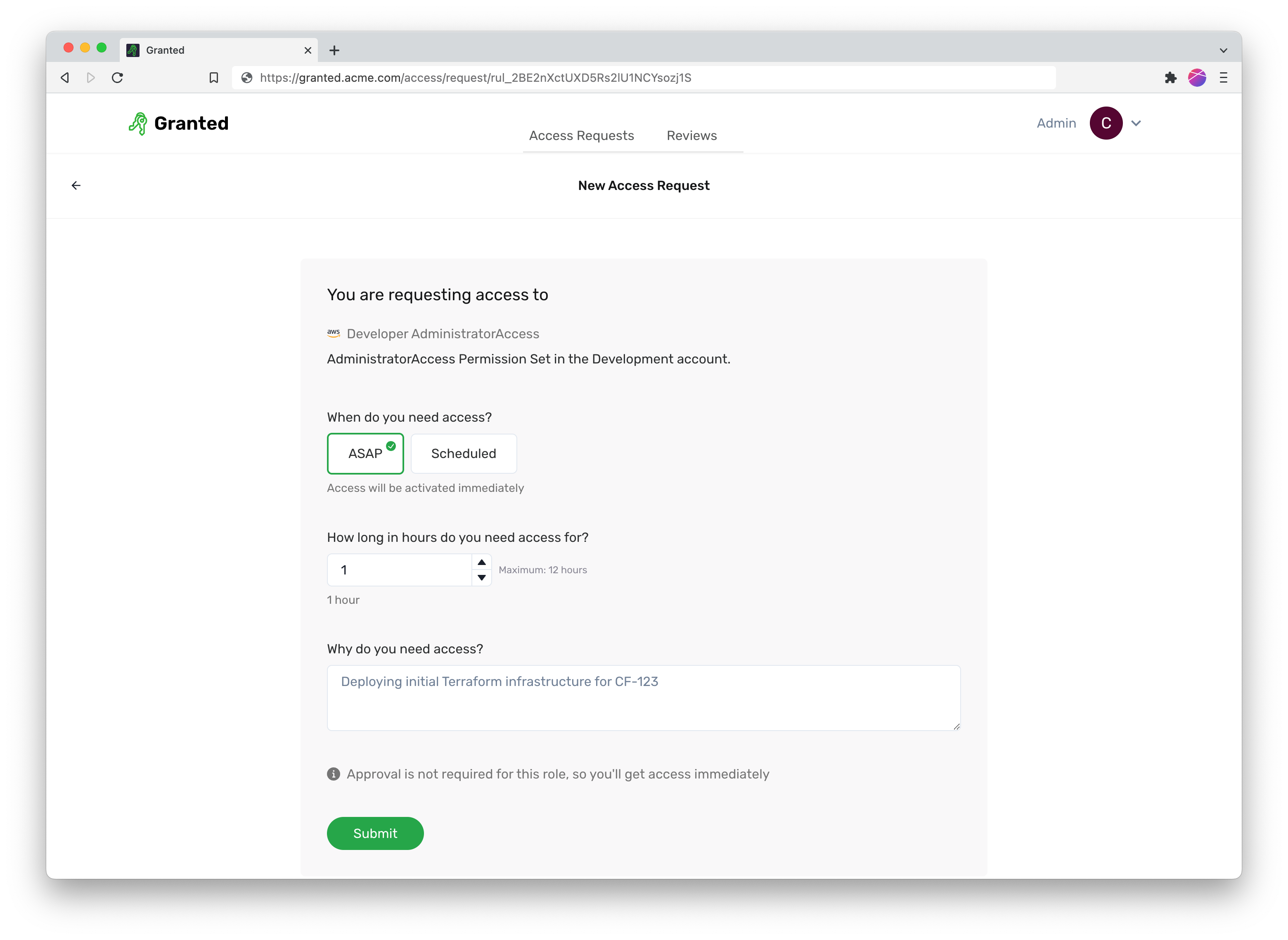
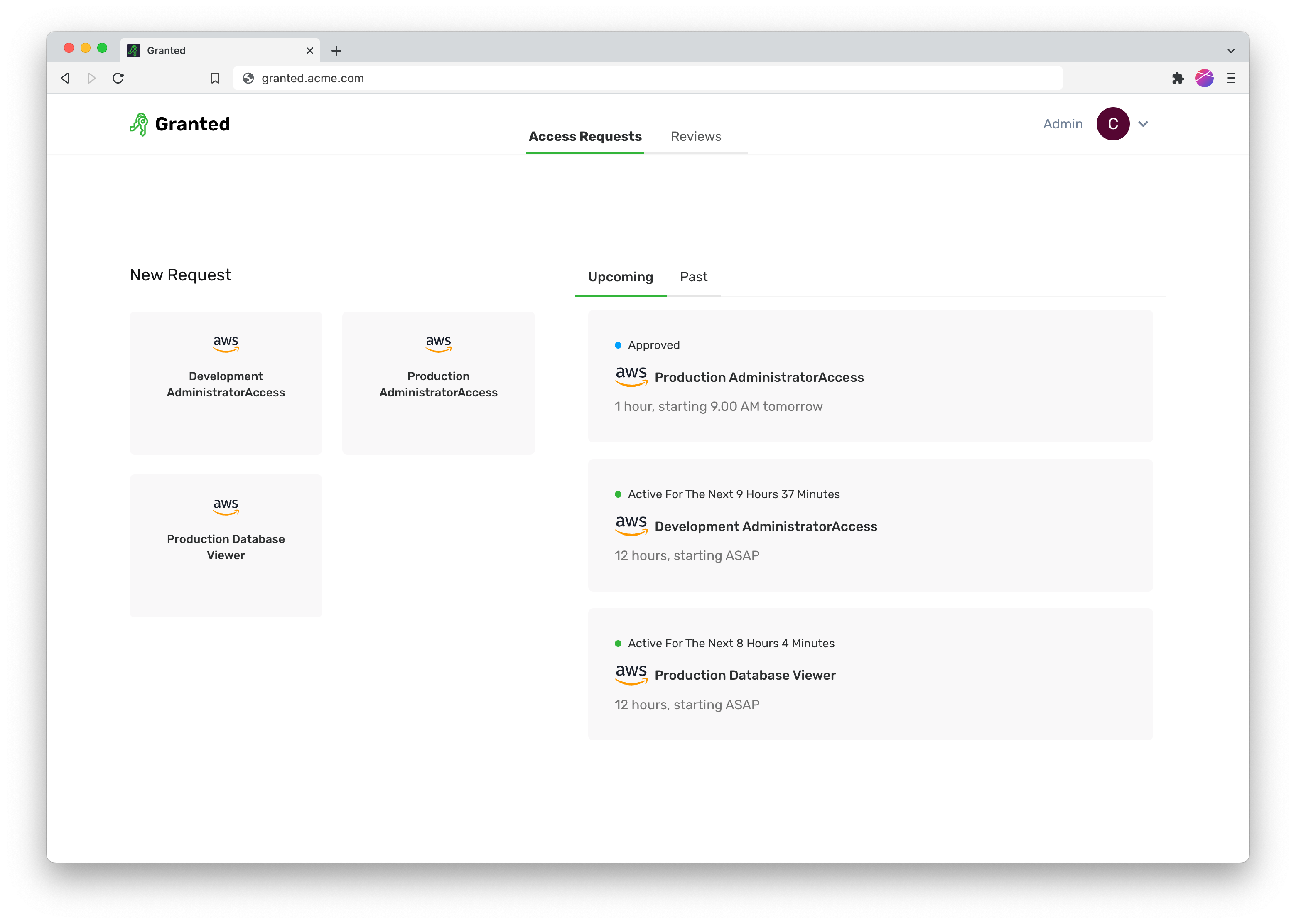
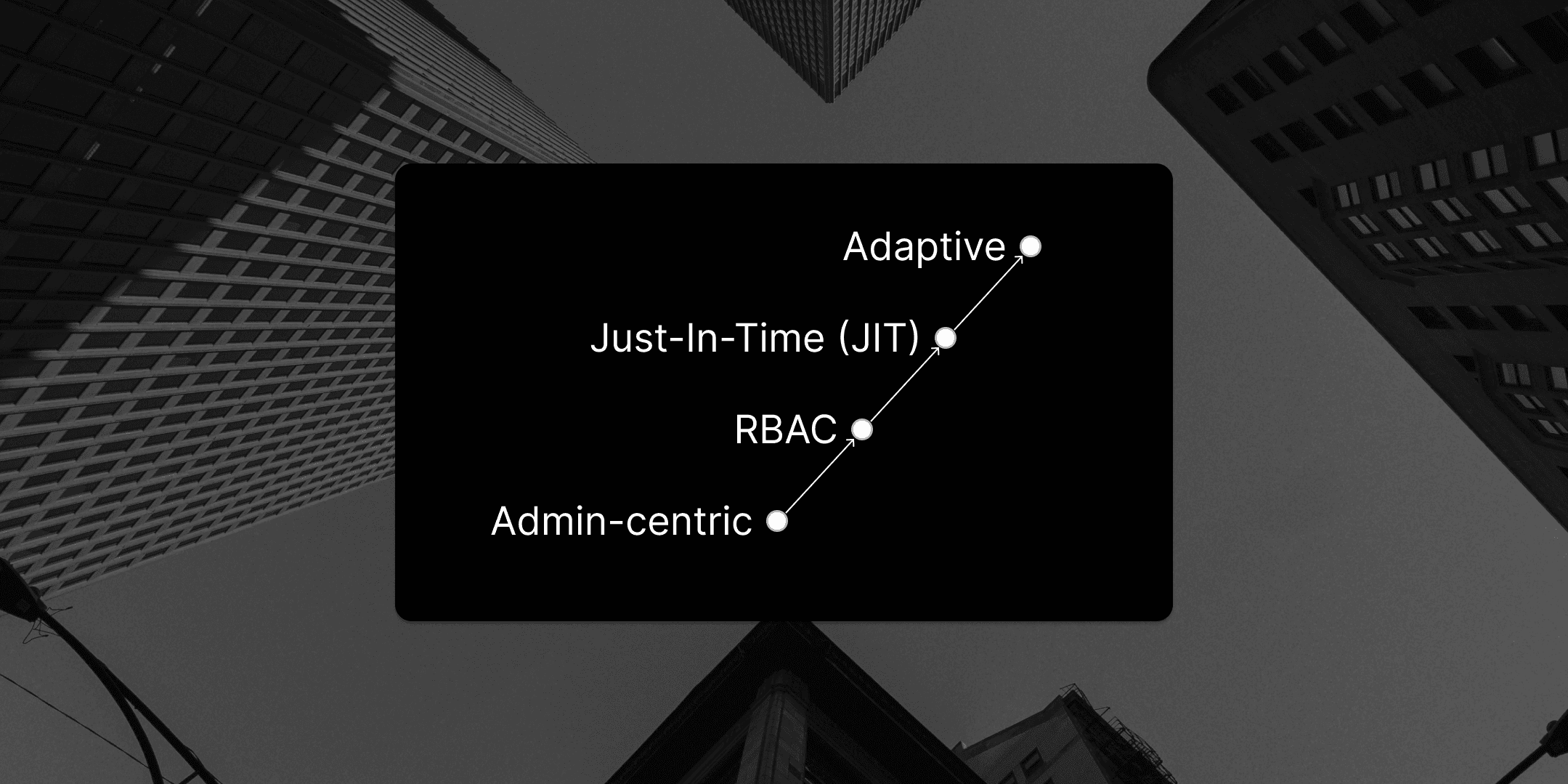
Granted Approvals is a privileged access management framework that you can self-host in your own AWS environment right now, today. We’ve worked hard to make this a tool that streamlines your access pipeline, with a key focus on:
Simplifying access: set up rules defining who can request access to what, and the resource owners who can approve access.
Seamless integration with your services: install Access Providers to provision fine-grain access to your SaaS services and cloud providers. Current support for AWS SSO, Okta groups, and Azure AD groups.
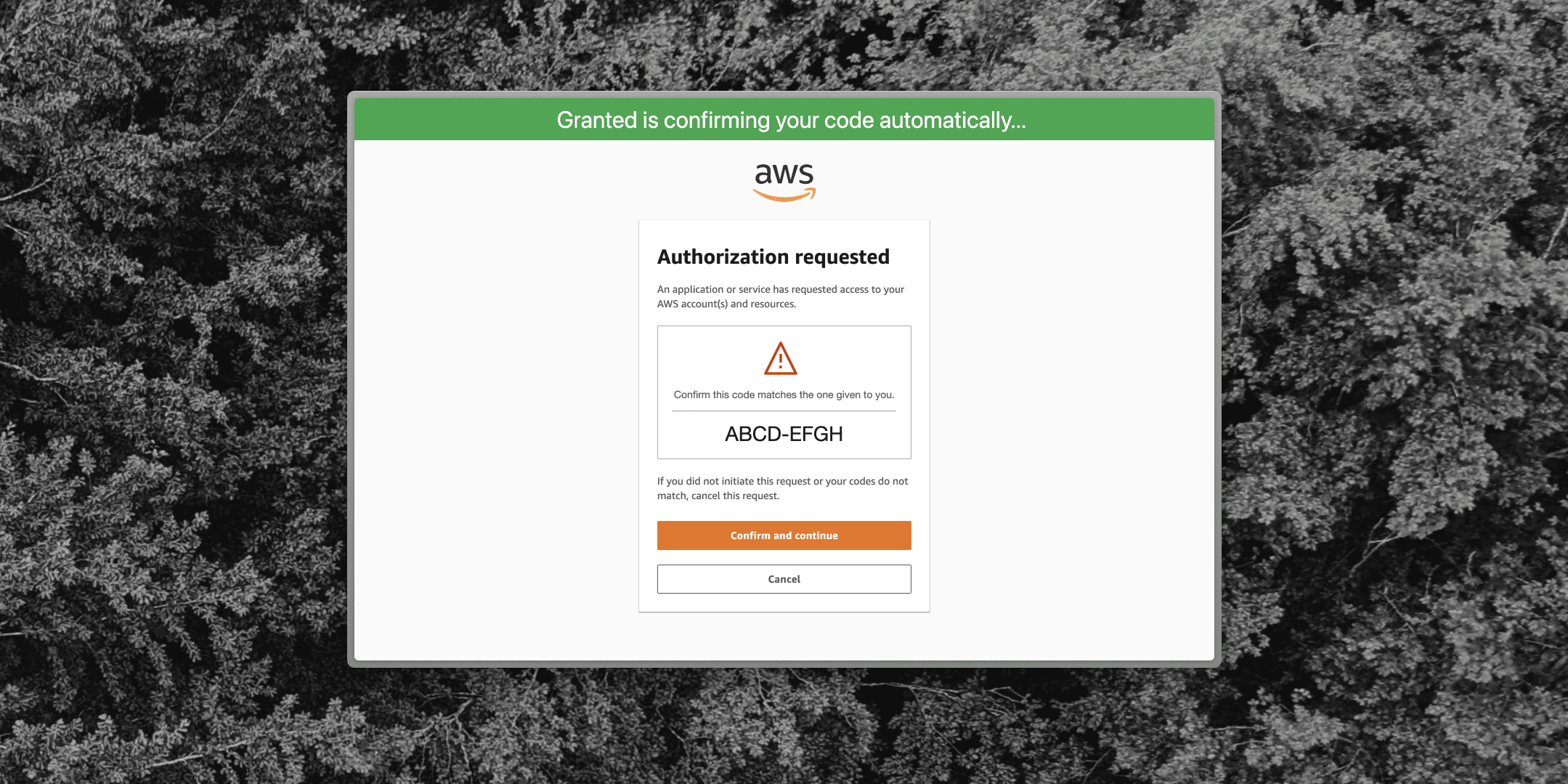
Fast and vocal approvals: approve access with just a few clicks, and connect to your team’s communication tools like Slack.
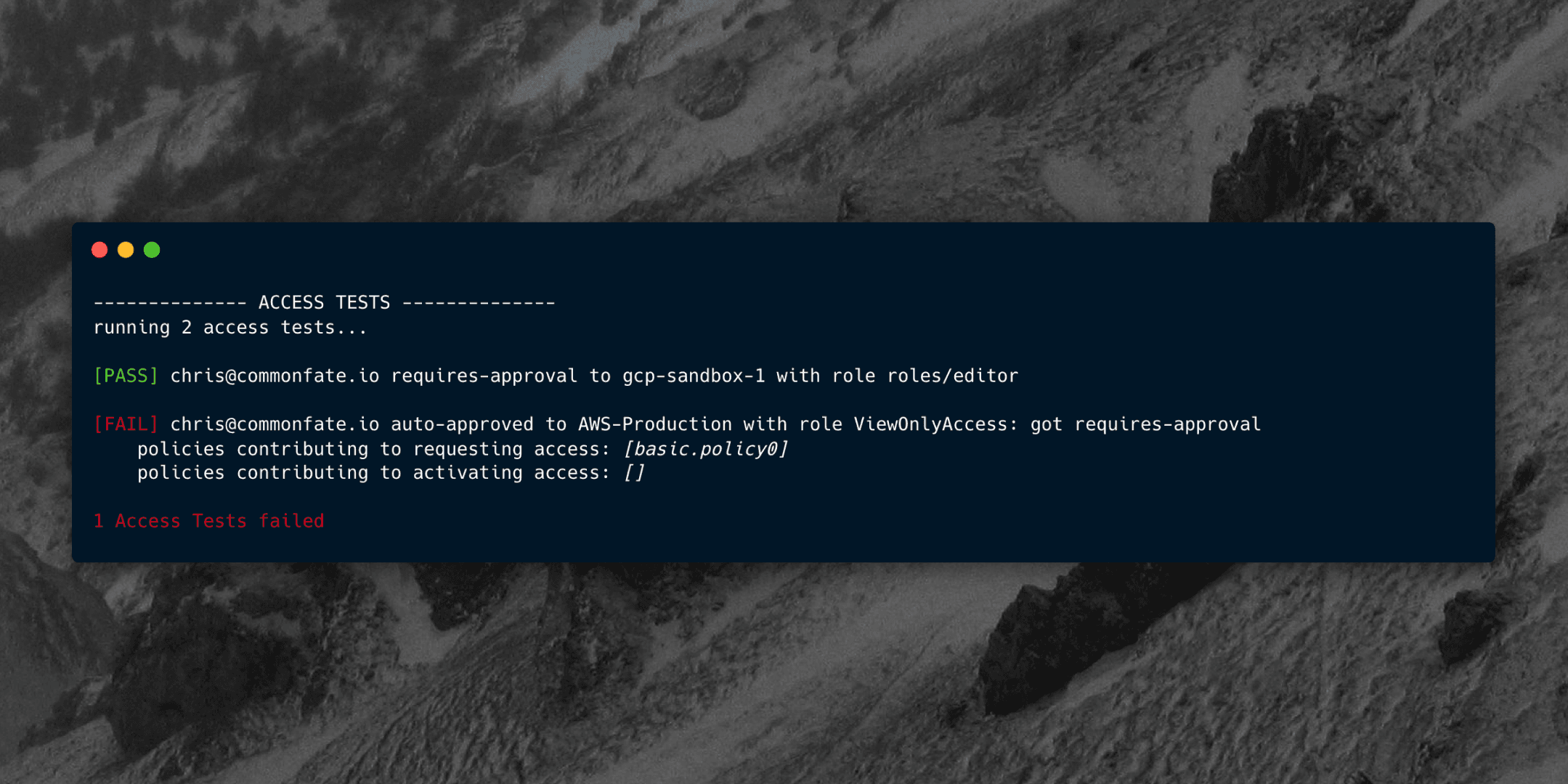
Auditability: see past and upcoming access requests. No more pulling all-nighters right before your ISO audits.
Concerned about security? Us too. We’ve designed Approvals so that it only has the ability to assign roles to existing users, rather than create new roles or new users. By design, the blast radius of Granted Approvals being compromised is that existing users in your directory could be granted access to roles, rather than external users being created. Better yet — Approvals is deployed as a serverless application which runs in your own AWS account, so Common Fate won’t have access to any data in your Granted Approvals deployment. Check out our Security Architecture page — and if you’re still not convinced, send us your concerns over Slack or Twitter.
You can get started with Approvals over at our Introduction page, or check out our Github repo. It’s still in early access, so we’d be totally chuffed if you’ve got any feedback or bug reports you want to send our way.
Stay in touch, and happy ClickOps-ing.